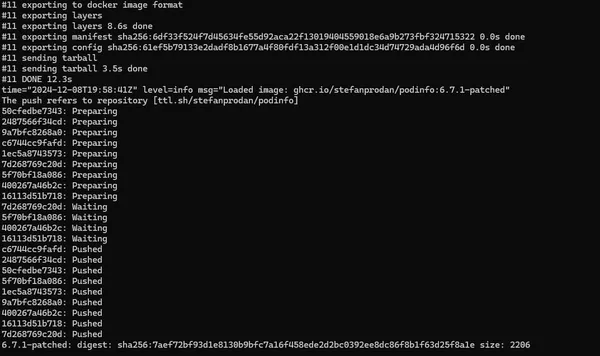
6 min read
Containers Automatically create patched images for containers in your cluster.

Automatically create patched images for containers in your cluster.
How to get a free cluster in the cloud.
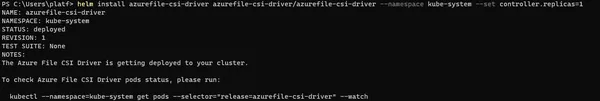
When testing in minikube, you may desire to be using the same tools that you are using in AKS.
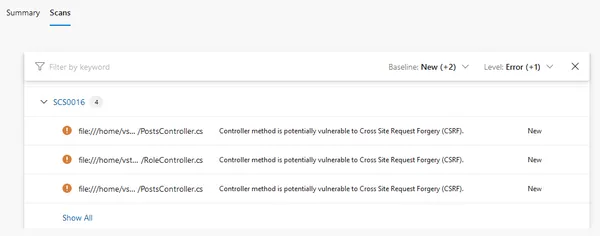
You've probably heard about other SAST tools like SonarQube, but since Security Code Scan is a lesser known tool I'll start off with a list of reasons why you might consider using it.
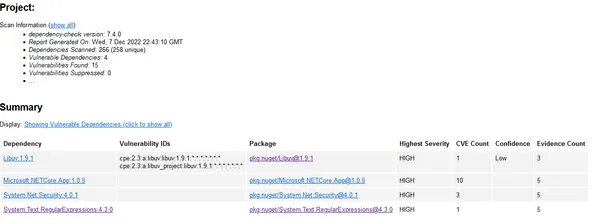
Have you ever wondered if your dependency scanning is checking for vulnerabilities beyond your immediate package references?